Regulatory IT Compliance Consulting
CyberWave is a full-service Global IT Security Compliance Consulting Firm providing regulatory compliance programs & cyber security compliance consulting services. Let us help you achieve IT compliance; we understand that every organization is different and work with our clients to ensure we implement the right regulatory compliance services and Solutions. Our managed compliance services will develop and maintain your security program based on the standards defined by legal mandates, contractual obligations, and internal policies and standards.
Our IT Regulatory Compliance Consulting services help clients identify vulnerabilities and assess real business risks, meet PCI, HIPAA, GLBA, FISMA, GDPR, NYDFS, ISO 27000 compliance, and other security compliance mandates more efficiently and effectively, devise security and governance programs that fit a client’s environment, and help them recover from and prepare for a cyber security breach.
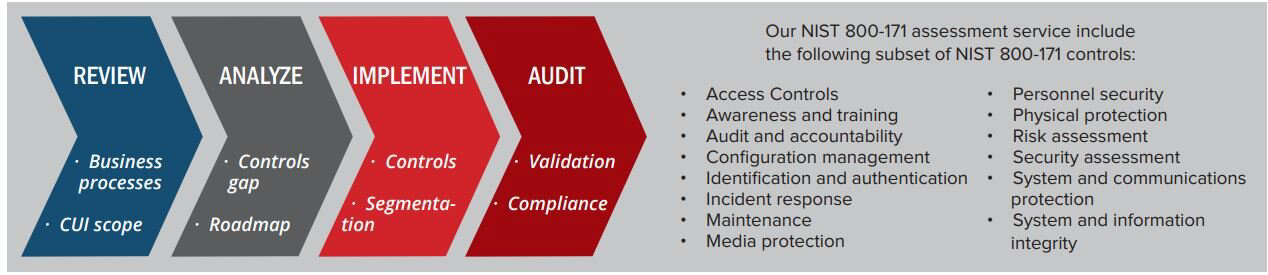
CMMC requirements apply to all DoD contractors and subcontractors. In other words, all contractors that perform under a contract that contains a CMMC requirement will be required to be certified under the program. DoD cybersecurity compliance, DFARS compliance, and NIST SP 800-171 compliance have become large-scale concerns for all Department of Defense (DoD) contractors since they were made effective in December 2017.
Deliver a unified view of cyber risk and vulnerabilities across your organization through risk-focused tools and procedures. Gauge the potential impact of risk-based decision-making on the mission. Reduce time spent obtaining DoD and other federal agency authorizations with reciprocal acceptance. Increase the likelihood of executing future projects on time and on budget by proactively building security into systems. Enhance efficiency through information assurance control inheritance and reuse.
Aerospace Defense Security solutions
No need to worry CyberWave provides all the services needed to get you in compliance: Nexgen Firewall, Advanced Threat Endpoint Protection, Managed Patch Management, 24/7 Monitoring and Maintenance of your systems, Business Continuity Plan and Systems, Security and Incident Response Team.
Aerospace Implement System Security Plans
Develop, document, periodically update, and implement system security plans for organizational information systems that describe the security requirements in place or planned for the systems.
Risk Categorization: Organizations must categorize their information and information systems in order of risk to ensure that sensitive information and the systems that use it are given the highest level of security.
System Security Plan: DFARS NIST 800 requires agencies to create a security plan which is regularly maintained and kept up to date. The plan should cover things like the security controls implemented within the organization, security policies, and a timetable for the introduction of further controls.
Security Controls: DFARS NIST 800 outlines an extensive catalog of suggested security controls for NIST compliance. NIST does not require an agency to implement every single control; instead, they are instructed to implement the controls that are relevant to their organization and systems. Once the appropriate controls are selected and the security requirements have been satisfied, the organizations must document the selected controls in their system security plan.
Risk Assessments: Risk assessments are a key element of DFARS NIST’s information security requirements. NIST 800 offers some guidance on how agencies should conduct risk assessments. According to the NIST guidelines, risk assessments should be three-tiered to identify security risks at the organizational level, the business process level, and the information system level.
Certification and Accreditation: NIST requires program officials and agency heads to conduct annual security reviews to ensure risks are kept to a minimum level. Agencies can achieve NIST Certification and Accreditation (C&A) through a four-phased process which includes initiation and planning, certification, accreditation, and continuous monitoring.